How do I configure Refapp for Single Sign-on?
In this guide, we'll walk you through the necessary information and steps to configure SSO in your Refapp account.
We'll start by providing you with essential information and preparation steps. Then, we'll dive into how to set up SSO in your account, including detailed instructions for different identity providers.
Finally, we'll explore additional SSO add-ons for enhanced functionality. Let's get started!
If you already know which SSO type to configure for your account and want to skip ahead, click on the name of the SSO under the "How to Configure SSO in Your Account" section in the table of contents. This will take you directly to the instructions on configuration.
Table of contents
Information and preparation for configuring SSOSupported SSO Identity providers
Where in the system do I configure SSO?
What changes when SSO is activated?
Do I need to prepare anything before configuring SSO?
Configuring your identity provider
Supported SSO Identity providers
Refapp supports single sign-on through the SAML 2.0 interoperability standard.
The vendors currently tested and supported are:
- Microsoft Entra ID (formerly Azure AD)
- Microsoft Active Directory Federation Services (AD FS)
- Octa Auth0
Where in the system do I configure SSO?
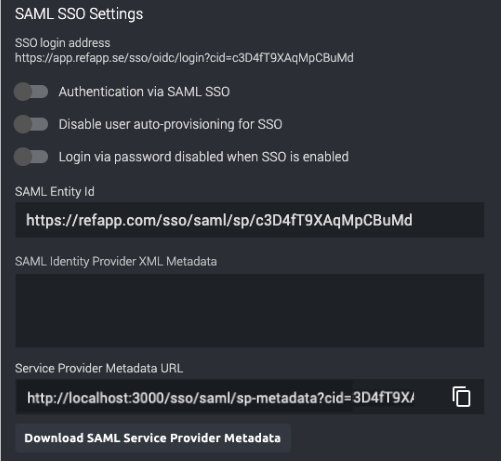
New section in Company Settings
As a Refapp Administrator, you can manage all the SAML SSO configurations from your Company Settings page and its SAML SSO Settings section.
The master switch is named Authentication via SAML SSO.
Authentication via SAML SSO
This is the master switch. When enabled and if there is valid metadata, logins via SSO will be enabled.
Disable user auto-provisioning for SSO
When turned on, new users will need to be created manually by you on the Refapp Users page. When turned off, users are automatically created in Refapp when they log in the first time.
Login via password disabled when SSO is enabled
When this switch is turned on and SSO is enabled, users can no longer log in using their existing passwords.
SAML Entity ID
The default value for entity ID is an automatically generated unique value like the one in the picture below.
SAML Identity Provider xml Metadata
Paste the content of the xml metadata file that you download from your SAML identity provider into this field.
What changes when SSO is activated?
This is what changes when SSO is enabled.
- Users can no longer log on using passwords (unless “Login via password disabled when SSO is enabled” is left in an off state) or change their passwords through Refapp.
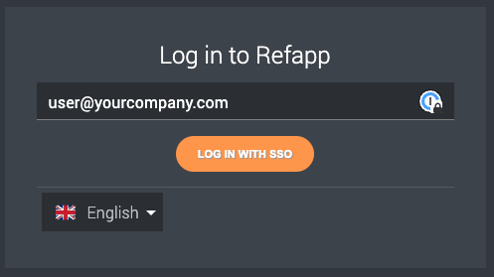
- When the system detects a mail domain belonging to your company, the login user interface will change to show only a button that takes the user to your company login page. If the login is successful and it has been validated that the user is provisioned to use Refapp, they will be logged into Refapp and can use the system as usual.
- If “Disable user auto-provisioning for SSO” is left deselected, users can no longer be invited from the Refapp Users page
- The cached Refapp login token (stored in-browser) for SSO-enabled companies will expire after 24 hours (instead of 30 days for user/password logins) at which point the system will trigger a renewed login with your SSO system. This ensures that users can be offboarded properly.
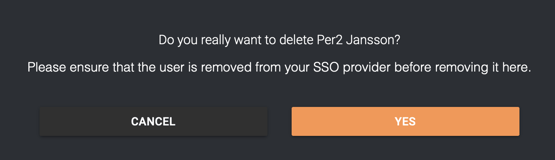
- If you need to expedite offboarding, you can delete a user from Refapp through the Users page after removing the user’s access to the application in the SSO application. All user sessions will be terminated immediately. If you keep the user’s access and remove the user from Refapp, a brand new user with the same name will be created at their next login. This will lead to confusion.
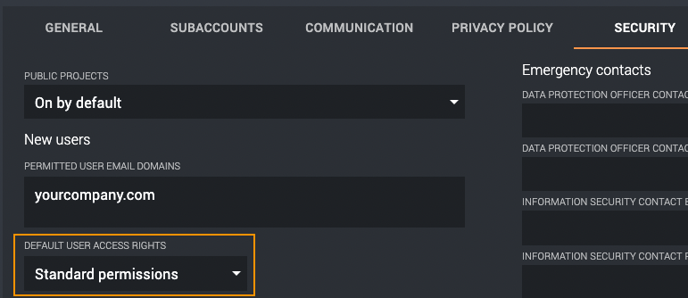
- If you have left the company setting Disable user auto-provisioning for SSO turned off, new users are onboarded automatically at login time and will be assigned the Default user access rights set on the Company Settings page. If they need extended permissions, your company’s assigned admin users need to perform that action through the Users page in Refapp after they have logged in the first time.
- Users get a new option to log out completely from the SSO provider at the bottom of the profile page.
Do I need to prepare anything before configuring SSO?
Preparations
Ensure that you have set up the corresponding mail domains for SSO in Company Settings. Multiple domains, e.g. “brand1.yourcompany.com” and “brand2.yourcompany.com” are supported.
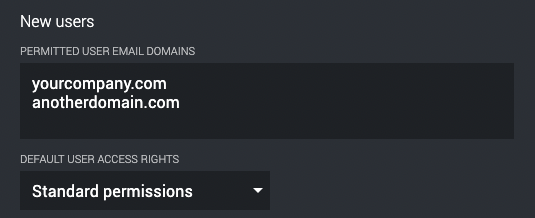
Configuring your identity provider
Click on the name of the SSO type to be redirected to the guide.
- Configuring Entra/Azure AD for Refapp SSO
- Configuring Microsoft Active Directory Federation Services for Refapp SSO
- Advanced settings and configuration for other providers
